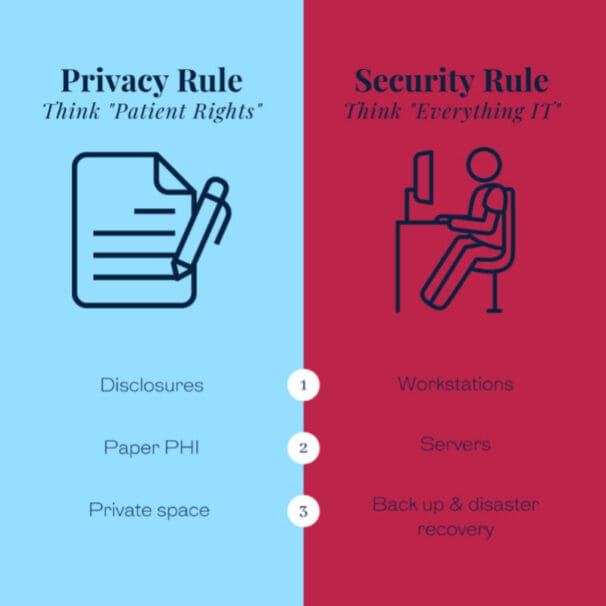
The Privacy Rule 45 CFR Part 164 Subpart E sets the standards for using and disclosing protected health information (PHI).
In contrast, the Security Rule 45 CFR Part 164 Subpart C explicitly sets the Security Standards for the Protection of Electronic Protected Health Information (ePHI).
Electronic vs. oral and paper
It is important to note that the Privacy Rule applies to all forms of patients’ protected health information, whether electronic, written, or oral.
In contrast, the Security Rule covers only protected health information in electronic form (ePHI), including ePHI created, received, maintained, or transmitted electronically.
The Security Rule sets the standards for ePHI transmitted over the Internet and stored on a computer, but it does not cover PHI stored on paper or provided orally.
The HIPAA Privacy Rule
The Privacy Rule requires appropriate safeguards to protect the privacy of protected health information and sets limits and conditions on the uses and disclosures that may be made of such information without an individual’s authorization.
- 45 CFR Part §164.504 Uses and disclosures: Organizational requirements.
- 45 CFR Part §164.506 Uses and disclosures to carry out treatment, payment, or health care operations.
- 45 CFR Part §164.508 Uses and disclosures for which authorization is required.
- 45 CFR Part §164.509 Uses and disclosures for which an attestation is required.
- 45 CFR Part §164.510 Uses and disclosures requiring an opportunity for the individual to agree or to object.
- 45 CFR Part §164.512 Uses and disclosures for which an authorization or opportunity to agree or object is not required.
- 45 CFR Part §164.514 Other requirements relating to using and disclosing protected health information.
The Rule also gives individuals rights over their protected health information, including rights to examine and obtain a copy of their health records, to direct a covered entity to transmit to a third party an electronic copy of their protected health information in an electronic health record, and to request corrections.
- 45 CFR Part §164.520 Notice of privacy practices for protected health information.
- 45 CFR Part §164.522 Rights to request privacy protection for protected health information.
- 45 CFR Part §164.524 Access of individuals to protected health information.
They must reasonably safeguard PHI from any intentional or unintentional use or disclosure that violates the Privacy Rule standards, implementation specifications, or other requirements.
A covered entity must also reasonably safeguard to limit incidental uses or disclosures of PHI made under an otherwise permitted or required use or disclosure.
- 45 CFR Part §164.526 Amendment of protected health information.
- 45 CFR Part §164.528 Accounting of disclosures of protected health information.
- 45 CFR Part §164.530 Administrative requirements.
- 45 CFR Part §164.532 Transition provisions.
The HIPAA Security Rule
The Security Rule establishes national standards to protect individuals’ electronic personal health information created, received, used, or maintained by a covered entity.
- 45 CFR Part §164.306 Security standards: General rules.
- 45 CFR Part §164.314 Organizational requirements.
- 45 CFR Part §164.316 Policies and procedures and documentation requirements.
The Security Rule requires covered entities to reasonably implement appropriate Administrative, Physical, and Technical safeguards to ensure the confidentiality, integrity, and security of electronically protected health information.
- 45 CFR Part §164.308 Administrative safeguards.
- 45 CFR Part §164.310 Physical safeguards.
- 45 CFR Part §164.312 Technical safeguards.
- Appendix A to Subpart C of Part 164 — Security Standards: Matrix
The Security Rule provides details and security requirements that are far more comprehensive than the Privacy Rule. As covered entities begin privacy compliance planning initiatives, they should consider assessing the security compliance initiatives they have implemented. Covered entities that have implemented the Security Rule requirements have already taken some measures necessary to comply with the Privacy Rule.
Enforcement
The Federal requirements preempt state laws contrary to the Privacy and Security Rule unless a specific exception applies.
The Office for Civil Rights (OCR) within the Health and Human Services (HHS) enforces the Privacy Rule. At the same time, the Centers for Medicare & Medicaid Services (CMS) oversees and enforces all other Administrative Simplification requirements, including the Security Rule.